Your Best Practices for Information Security Risk Assessments
- Written by: Trevor Meers

If you’re considering how to get the most value from your information security risk assessment—or whether you even need one—use these best practices shared by HBS vCISO Ben Hall. Ben and the rest of the HBS team conduct numerous information security risk assessments each year, giving them deep insight into how you can maximize this key part of your cybersecurity strategy.

Ben Hall
vCISO, HBS
Q: What’s the most common risk you see?
Ben: We always see issues with access controls, whether that be access to the network, access to applications or access to the facility. There is always some gap in control when it relates to giving an individual user access to those resources. A lot of times, we see organizations give administrator privileges to an end-user that may not be doing development activities. So not only can they make changes to their local workstation, but they can also make changes to an application or to something like customer data when it may not be necessary for their job role.
Q: What’s another common challenge that comes up in assessments?
Ben: Change management comes up a lot as well. A lot of organizations think they have pretty robust change management controls in place, but we can typically identify that it’s not the case when we ask for selections. So if it’s firewall changes and you make changes every Wednesday, we’re going to ask if there are tickets to back that up. If you’re doing development changes where you’re going from one version to another, where’s the development process within that? How are you evaluating that the development change is actually good and will fit within the environment? Is there a quality assurance (QA) test?
Q: Are there other policies or controls that you recommend everyone should have based on all the risk assessments you perform each year?
Ben: Incident response comes up now more than ever based on all the news we’re seeing, the ransomware events, the actions of malicious employees, etc. With all that going on, it’s crucial to be able to get your team together and properly respond to an incident.
Q: What kinds of things tend to surprise IT leaders when they read the report from their IT risk assessment?
Ben: They almost always find something surprising in there. Most people tend to think their environment is more secure than it really is. And that’s the benefit of bringing in a third-party for the risk assessment. We can provide that objective view. We’re not intimate with those controls, so we can ask the questions of why they exist in the first place. So the risk posture they expect versus the reality comes up a lot, and it can make those meetings a little interesting.
Q: You cast a wide net during a risk assessment by talking to people in a variety of departments. Why is it important to get all those perspectives within the organization?
Ben: Something that comes up often is a lot of shadow IT controls and applications that exist. You may be aware, for example, of what your Accounts Payable department is using to make sure all the statements are paid. But there may be additional things like cloud-sharing tools that you were unaware of and that the team tells the external auditor about. We also like to meet with the finance team and CFO or others in the C-suite to get that additional insight as to what’s existing today and what their expectations are for IT. It sheds a lot of light on what the CEO expects IT to do but has never told them about and that IT has never even considered.
Q: How do you coach people to read through a risk assessment report and start deciding on next steps?
Ben: One thing we do with every report is identify the 5-10 items that we’d start with if it was our program. So we help you set that prioritization focusing on Implementation Level 1: This is what needs to take place, all the way through. We also provide a risk register that lists any additional opportunities for improvement discovered through the risk assessment. So that way you not only have that executive overview of these 10 things to do immediately, but you have that other comprehensive list of activities that can be incorporated throughout the year.
Q: What trends have you been seeing in risk assessments this year?
Ben: The thing that surprises me the most is the lack of multifactor authentication across the board. You would think that with 2020 and that immediate shift to remote workforce, everyone would have widely implemented some kind of MFA or 2FA by now, I’m surprised that it’s still a gap with a lot of organizations that still have pretty substantial applications open to the network. A lot of times you’ll see that maybe they have put in some kind of VPN, but even that still doesn’t have MFA or 2FA tied to it. This remote shift is going to stay a while, so if you don’t already have plans to implement MFA or 2FA, that would probably be my #1 thing to start working toward this year.
Q: After an organization has done a risk assessment, when do they need to start thinking about another one?
Ben: Best practice is to do it at least annually. Even better practice is to have that annual risk assessment, but then have some kind of risk management committee. So not only are you evaluating those controls identified in the risk assessment and utilizing your risk register to manage a lot of that, but you’re also meeting on a quarterly or even monthly basis to look through what exists, adding new risks that have been identified throughout the year to that list and talking through a remediation plan. So you need that continuous evolution of quarterly processes reviewing that process in addition to the annual formalized risk assessment.
Q: Can an organization realistically evaluate its own risk using its internal team?
Ben: You could, and we often encourage that. But if you look at it like going to a gym and hiring a trainer, you really benefit from getting an expert opinion on what kind of workout makes the most sense for you. That can tie into risk assessments, too. You want that external opinion from subject matter experts who do this on a daily basis and can truly assess your organization with that independent lens. As a control owner within that organization, you tend to be a little guarded as far as to what some of those activities could be. In comparison, an independent auditor or assessor can look at those processes objectively and point out potential flaws that exist in the remediation activity. Hard questions will be asked during a good risk assessment. But that said, it’s not a tough engagement. We’re there to help you get better. So it’s best to give us those open, honest answers. We’re here to help you get stronger and get better. There are no wrong answers in a risk assessment.
If you’d like to talk with an HBS consultant about how to plan a risk assessment in your environment, contact us today.
Related Content
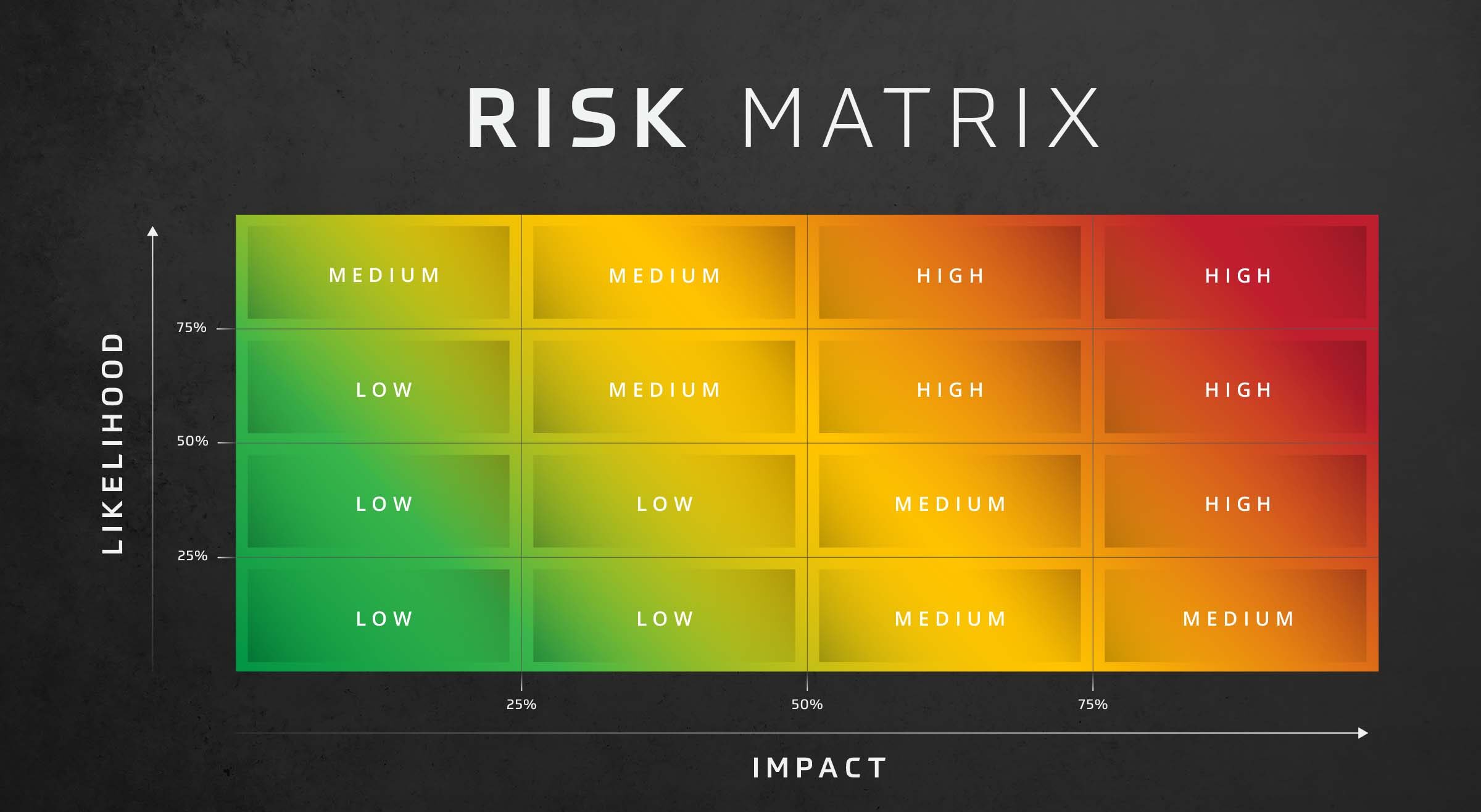
Risk Assessment: Likelihood and Impact
Assess risk effectively with the risk assessment likelihood and impact matrix. This decision-making matrix assesses risk based on the likelihood and impact of threats in your organization.

Cybersecurity Risk Assessment
Optimize your security with an HBS Cybersecurity Risk Assessment. Identify vulnerabilities, manage risks, improve your cybersecurity posture.

CISO Best Practices: Navigating Incident Response, Technology Integration, and Vendor Management
Dive into a panel discussion of CISO best practices, tips, and habits. Insights on incident response, technology integration, and vendor management.






