How to Train Employees With Simulated Phishing Campaigns
- Written by: Trevor Meers

Every advance in security technology reinforces a favorite industry cliché: It’s easier to hack people than servers. Clever code exploits may earn hackers bragging rights, but it’s a lot simpler to trick one user into clicking a bogus link and letting you in the front door.
That’s why social engineering continues to be the leading vector for cybersecurity incidents. Industry sources estimate that 80% of security breaches stem from phishing attacks and that 94% of malware arrives via e-mail.
It’s basic math for hackers. A bad actor can easily send out 1,000 e-mails at a time. If you assume an average ransom of $40,000, a success rate of even 1% yields $400,000. And in reality, phishing attacks can work 25% of the time.
Why do so many people fall for phishing e-mails every week? Human nature explains a lot of it. We’re baited with messages that threaten the loss of a service, promise a financial windfall, hint at an important message from our employer or play off our basic confusion about technical terms. All this is dangled in a familiar-looking message promising resolution with a single click.
And we shouldn’t stereotype all phishing victims as that co-worker who just doesn’t get it. Hackers have honed their game massively since the days of foreign princes asking you to help transfer money. Modern phishing e-mails often include your company logo, a trusted partner logo (such as Dropbox), your colleague’s authentic-looking e-mail address, details about your specific business unit and more. In some of our phishing tests, for example, HBS uses this convincing-looking Dropbox knockoff:

To stop e-mail phishing attacks, you must continually train your team to keep a wary eye on their inbox. That requires a combination of ongoing training and phishing simulations that keep everyone sharp. The first time you test employees with an internal phishing campaign, the results may be surprising. HBS’s phishing campaigns often hook 20% of the recipients into clicking the link, and we regularly see 10-15% of recipients giving up their credentials in a simulated attack.
How to Run a Phishing Campaign
Here are some key questions to help you plan an effective phishing campaign:
- Should I do it myself or hire a vendor? Multiple services let you create and execute your own campaigns. But hiring a partner lets you tap the expertise of teams who run dozens of campaigns each year.
- How often should I conduct campaigns? In short, regularly. Many organizations run them monthly, but quarterly tests are a good standard. It takes a lot of repetitions to keep your employees on the cutting edge of hackers’ tricks. Plus, you should be measuring your team’s progress in spotting phishing messages.
- Who should receive the test? In larger organizations, it often makes sense to target campaigns at specific departments using custom messages. One HBS client, for example, targets the IT team with decidedly more deceptive test messages, assuming these users should be far savvier. You also can customize messages to simulate the kinds of attacks you expect your team to see, such as fake invoices aimed at Accounts Payable.
- What are next steps for users who fail the test? Make sure follow-up messages take a tone of coaching, not shaming. And consider the timing of training. You can set up a campaign to send someone straight to training if they click a fake link, for example. But if you’re in the midst of a larger campaign, that spreads the word that a phishing test is underway, tainting the results. Our experts frequently delay e-mails announcing required training until the test is over.
Creating Effective Phishing Text Messages
Once you’ve planned the test logistics, it’s time for the art of the project. Your phishing campaign is all about testing users’ ability to spot a fake, which makes the quality of test messages central to the process. Here are several tips for effective test messages:
- Use a tool with plenty of templates. Top-level phishing campaign platforms like HBS’s offer hundreds of e-mail templates rated by difficulty. They can take an official angle, such as asking someone to log into a fake company VPN. Or they can use a personal focus, such as telling users an Amazon delivery failed or offering them a great rate on a loan from a local bank.
- Mix up the templates. If you follow the advice above and test regularly, you need a wide selection of templates to keep it fresh.
- Test multiple attack vectors. Good tests dangle a variety of lures. Ask users to click on a link in the message. Try to get them to open an attachment. Request that they enter their credentials. A good campaign report shows how many users fell for each approach. A well-rounded test also includes pretexting phone calls and SMiShing (phishing via texts, or SMS messages).
- Tie tests to current events. Hackers love capitalizing on the news with offers of Covid-related financial relief, promises of free sports tickets, etc. Your tests should simulate these tactics.
- Customize templates with convincing details. If you’re testing savvy users, put your company logo in a message asking them to log into the company VPN. You can even add a downloadable file that displays a message on the users’ screen when they run the bogus .EXE file.
- Target specific user groups. Hackers will do this, so your tests/training should cover this tactic. Use simulated spearfishing attacks, which include user-specific information. (If you’re testing executives, you can use the cool term of “whaling.”)
What to Learn From a Phishing Campaign
A good phishing campaign report includes a detailed summary like this:
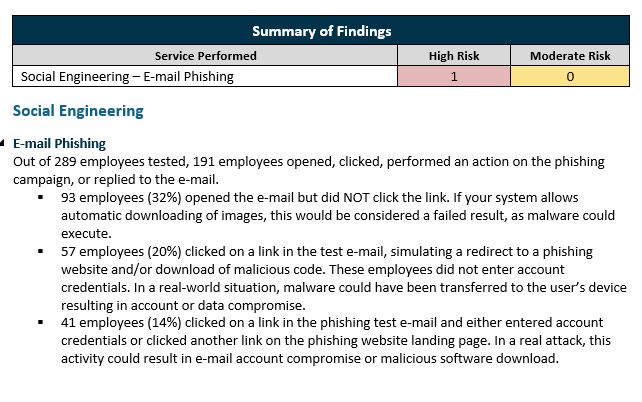
Some phishing solutions include an Outlook extension that users can click to report a phishing e-mail. Your IT team can track how many users report the test message as potential phishing, letting you measure their growing participation in spotting the problem. This kind of detailed information also lets you provide training targeted at the groups and individuals in your organization who are struggling to spot bogus e-mails.
Are you ready to learn how HBS’s experts can help your organization train and test your team’s security awareness? Check out our services or contact us today! Every advance in security technology reinforces a favorite industry cliché: It’s easier to hack people than servers. Clever code exploits may earn hackers bragging rights, but it’s a lot simpler to trick one user into clicking a bogus link and letting you in the front door.
Related Content

Don’t Get Hooked by Phishing: Identify Safe Internet Domains
Learn how to evaluate URLs, recognize phishing domains, and stay safe online. This guide breaks down internet domains and offers tips to avoid phishing scams.

How a Hacker Conned an Accountant with $400,000 Phishing Attack
See how the hacker got away with a small fortune for nearly a week—and how good incident response and digital forensics work got most of it back.

What Is a Human Firewall?
A Human Firewall is your first line of defense against cyber threats. Learn how to train employees to spot phishing, report suspicious activity, and build a strong security culture.