Internal vs. External Threats – Which One Worries You More?
- Written by: Dave Nelson

The age-old battle of insider threat vs. external threat rages on between information security professionals. The ongoing musings around information security in the Wikileaks and Richard Snowden cases continues to be debated in various forums. Where do you stand? Are you more worried about information security threats from internal or external sources?
There are arguments for each side
First look at the facts. The Verizon Data Breach Investigation Report indicates that organizations are much more likely to experience a breach from an external source. Target for example wrote off $148 million related to their breach. Some of you will say "Hah...case closed, told you so." You may not be wrong in saying that. But the same report also shows that the cost of an internal breach is more than the average external breach. This is where the other side says "Take that...I knew we were right." So who is really correct in their argument? I say both and neither. The 2015 DBIR show a singular correlation for information security breach costs. The total number of records lost is the key to your costs and therefore a large part of your risk equation. Your organization must determine if there is a greater risk of record loss from internal or external sources. There is no right or wrong answer.
Approaching risk from different perspectives
I say it really depends on perspective. You could simply look at the situation from the narrow threat perspective. If you are a small family run company, external information security threats are probably a bigger concern than if you're a mid-sized company that treats their employees like garbage and has a very disgruntled workforce. Who's more likely to have a threat of internal or external attack?
If however you take a broader approach and think of risk in terms of threats who take action on vulnerabilities against an asset, you may look at things differently. What vulnerabilities exist? What administrative, physical or technical controls have you put in place to defend against threats? As you work through your risk management you should realize that information security is about balance and compromise.
A balanced approach to addressing threats
If we place too much emphasis on one threat or vulnerability we risk exposing our organizations in other areas. We must take a balanced approach to addressing threats whether they are internal or external. To some degree, we also need to ignore what others may see as a threat to their organization's information security. In the real world, no two situations are alike. No two companies are alike. No two threats are alike. The best thing you can do is to understand the full picture of the overall risks your company faces and deal with them in a way that works for you.
Related Content
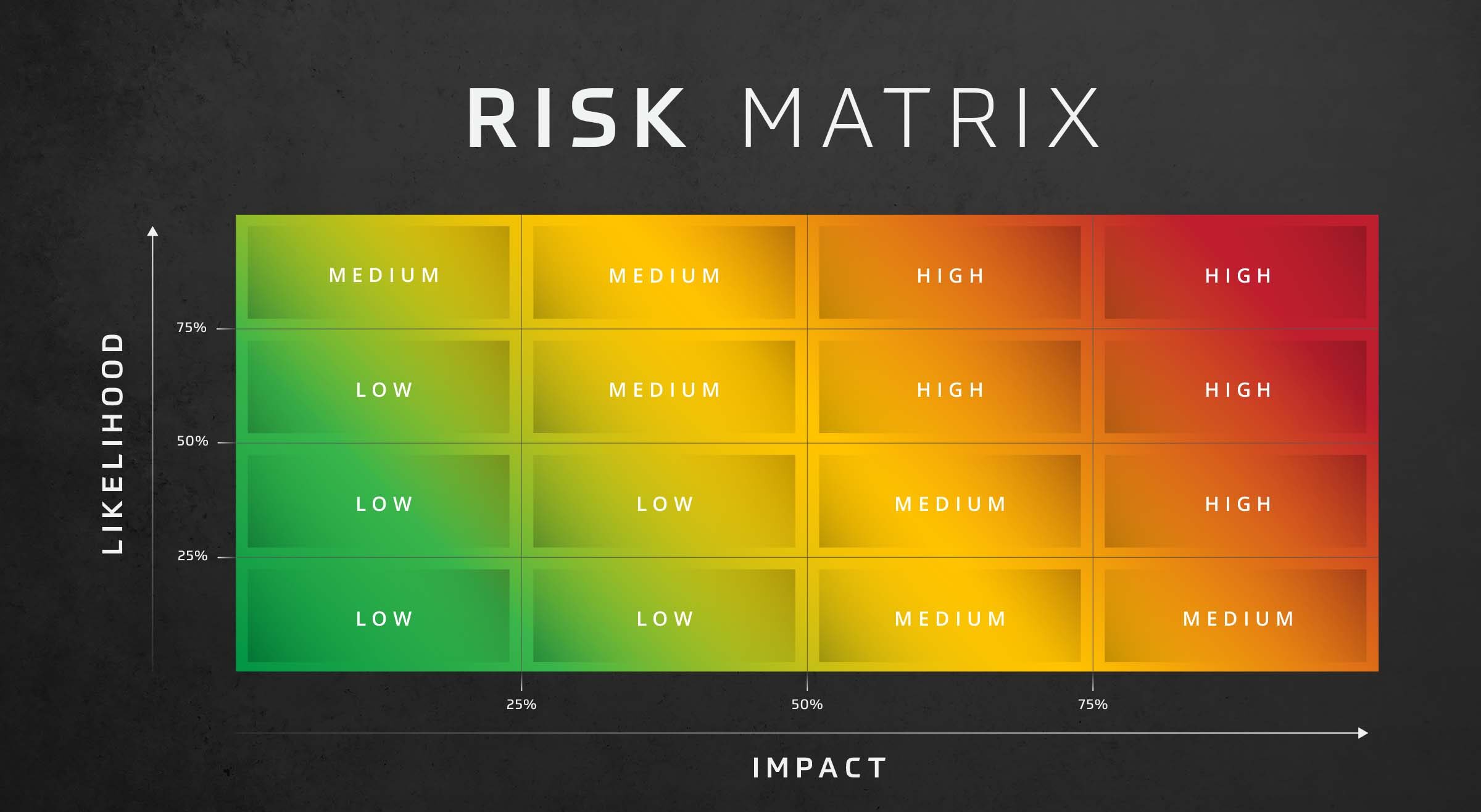
Risk Assessment: Likelihood and Impact
Assess risk effectively with the risk assessment likelihood and impact matrix. This decision-making matrix assesses risk based on the likelihood and impact of threats in your organization.

Cybersecurity Risk Assessment
Optimize your security with an HBS Cybersecurity Risk Assessment. Identify vulnerabilities, manage risks, improve your cybersecurity posture.

IT Company Assessing Risk to Protect Clients
A company managing clients’ IT infrastructure can’t afford a breach. That’s why this IT solution provider took recommendations from their colleagues and hired HBS to conduct a risk assessment.






