Mergers and Acquisitions (M&A) Now Including Cyber Security Due Diligence as Best Practice
- Written by: Jordan Engbers

There has been a surge in Mergers and Acquisitions (M&A) over the past couple years, and those numbers will continue to rise. So, what should companies be looking for as part of their due diligence? For years this answer has looked something like this: “Check the financials, legal and intellectual property...” But now, cyber security practices and technologies are at the forefront of these same conversations.
The thought of acquiring a company can be very exciting. An acquisition can help a company gain a stronger foothold in a familiar market or branch out into new geographic regions. In other instances an acquisition will enable a company to add complementary products/services to diversify their portfolio. Regardless of the strategy, the goal of an acquisition is to improve the acquirer’s current state. And the target company can be seen as a means to that end.
The Impact Cyber Security Practices Can Have On Financials
If, however, a company limits itself to only focus on the target’s financials, it may become blinded by seemingly strong financial statements while overlooking cyber security risk, even though the risks posed by an existing or potential security breach could significantly impact financials far into the future. So, what does this mean to an acquiring company? Limiting the due diligence process in a way that neglects security practices and technologies could greatly overvalue the target company and pose significant risk. Without a cyber security assessment, it can take several months or even years for an organization to discover that it has experienced a security breach. If proper action isn’t taken to evaluate and assess the target’s security posture, the acquisition could become a serious failure and cost the acquiring company millions of dollars.
Cyber security and IT issues are a major risk factor for any acquisition. Buyers should engage technology / security experts to determine these risks and quantify the effect on the target’s operations, which can be significant.
Paul Juffer, CPA
Managing Partner - LWBJ
Valuating a Company Based on Complete Information
It is imperative to ask the right questions and perform an appropriate cyber security assessment prior to landing a deal. From the outside, the target company may look healthy, but in reality the target’s information could be compromised, leaving only a matter of time before client data is being sold on the dark web or intellectual property is being copied and produced overseas. As the purchaser, if cyber security risk is discovered, you can use the information gained in the due diligence process to value the company at a discounted rate or you can decide to walk away entirely. Of course, it will depend on the severity of the risk. Unfortunately, if this discovery occurs after the close of the acquisition, the acquiring company will be left picking up the pieces. This is why it is so important to perform an assessment early in the process.
IT Due Diligence Assessment
An IT Assessment will consist of assessing the controls and operational effectiveness and efficiency. It is important to perform an internal assessment of IT infrastructure to assess the confidentiality, integrity and availability capabilities of connected systems. The specific areas tested should include the following:
- Network, server, and device security, including event monitoring
- Disaster Recovery Plans, Data Backup and Restore, and Business Continuity Plans
- Encryption of sensitive data
- Segregation of duties, minimal access, and other Role Based Access Controls (RBAC)
- Physical security controls (cameras, locks, lighting, etc.)
Performing an assessment of security and risk management policies to ensure adequate controls are used to ensure information security is also a critical portion of the IT due diligence assessment. Policies to be reviewed should include:
Technology
- IT Risk Management Program
- Policies, Procedures, and Standards
- Change Management
- Vulnerability Management and Incident Response Plans
- Vendor Management
Human Resources
- Employee Background Check and Onboarding Checklists
- Employee Security Awareness Training
- Employee Transfer and Off-boarding Checklists
If you are considering acquiring a company, make sure you consider all of the factors that impact valuation, including cyber security practices and technologies. And, if you are looking to sell your company, make sure to have your own IT Due Diligence Assessment performed. This will enable you to take appropriate steps to reduce your company’s IT risk and improve the valuation of your business prior to negotiations with a suitor.
Need help with cyber security and IT due diligence? We can help.
Related Content

HBS’s vCISO Service Guides Marketing Firm Through Rapid Growth
Rather than building a costly in-house team, executives chose the flexibility and broad expertise of virtual CISO service for the long haul.

Why Consider Live Acquisition for Your Next Digital Forensics Case
Explore the evolving landscape of digital forensics, including live system analysis and the impact of encryption. Learn how technology changes have shifted our approach to forensic examinations.
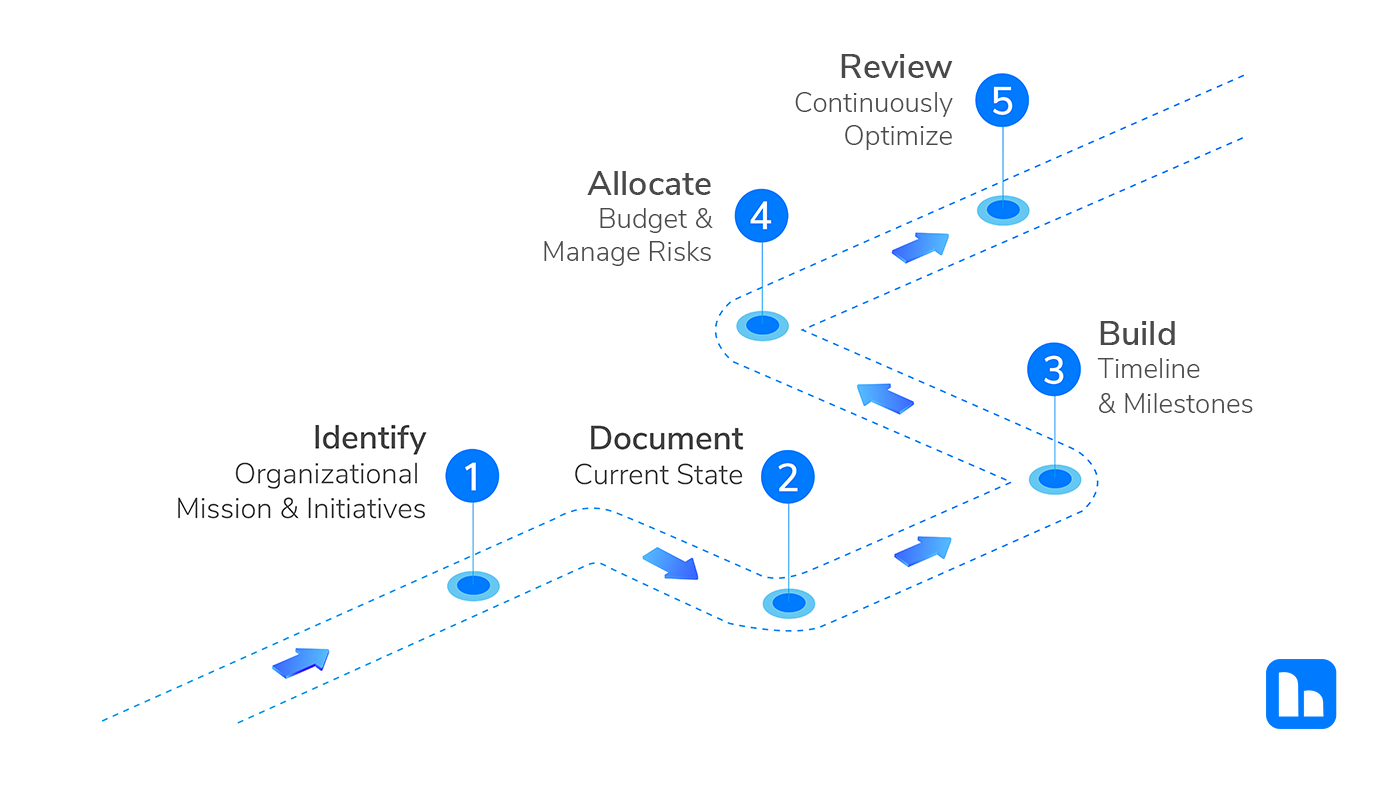
IT Strategy Roadmap: Why Every Business Needs One
Struggling with IT alignment, security, and innovation? An IT strategy roadmap means optimize resources, scalable business growth, and digital transformation.