What is Source Code Escrow and Why Do I Need It?
- Written by: Dave Nelson
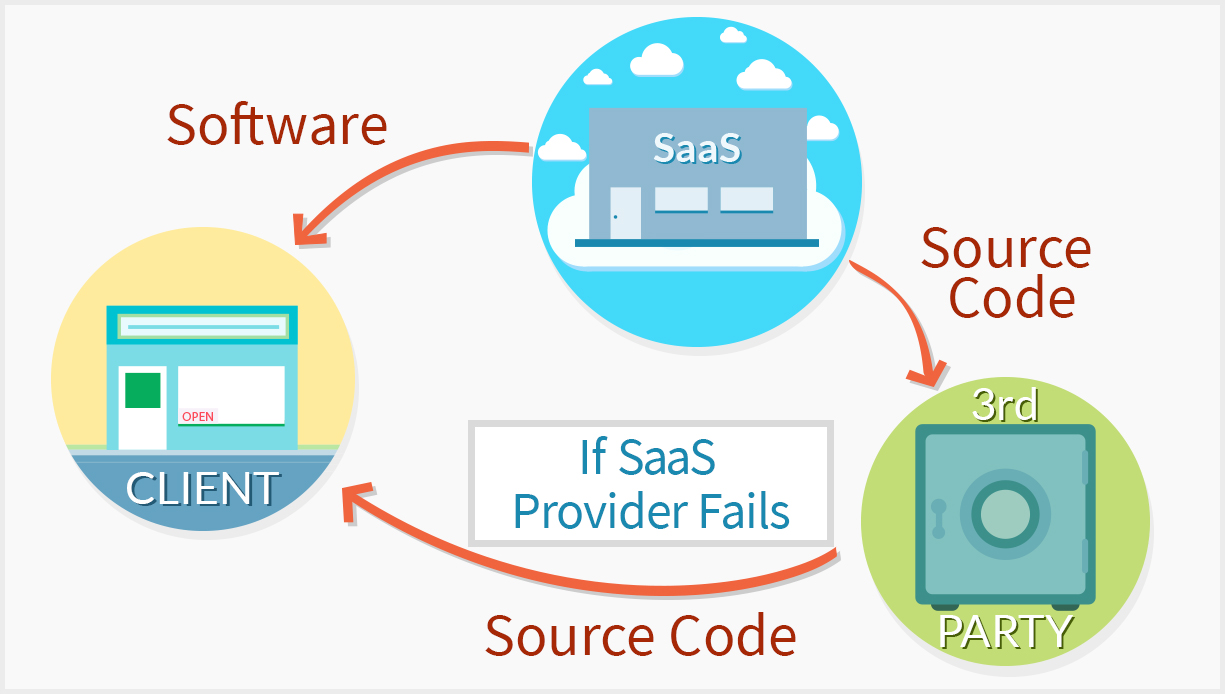
Source code escrow is a process by which a company that wants to sell cloud applications or Software as a Service (SaaS) can provide peace of mind to their clients. It is also a way for clients to hedge their bets to ensure business protection. The SaaS provider agrees to put their source code in escrow with an independent third party. In the event of bankruptcy, insolvency, receivership or other pre-determined business situations, the client may request access to the source code so that the application can be brought in house with the client, and business can resume.
Software Licenses of the Past
In the past, clients purchased perpetual licenses for business critical applications, deeming source code escrow unnecessary. The licenses were installed on systems owned and managed by the clients. If the software vendor abruptly closed their doors, the client could still continue their day to day business. The source code was not needed by the client because the compiled application was running just fine in its current environment.
Software Control Now and in the Future
In the SaaS world, however, that same business critical application is now totally dependent on the vendor. The software is running on hardware owned by the vendor. Should that provider go belly up, clients are left with nothing. They may not even have access to their data for a migration.
There are a lot of different source code escrow services. Some offer full review and testing of the code to make sure it works after every upload. Others are simply an independent third party repository that will work with the courts to release code should a triggering event occur. Offering source code escrow as a SaaS provider shows your clients you are committed to their success, regardless of what happens to you. As a SaaS client, making source code escrow a contract term will provide needed assurance that your critical business can continue in event of a catastrophic failure at your vendor.
Related Content
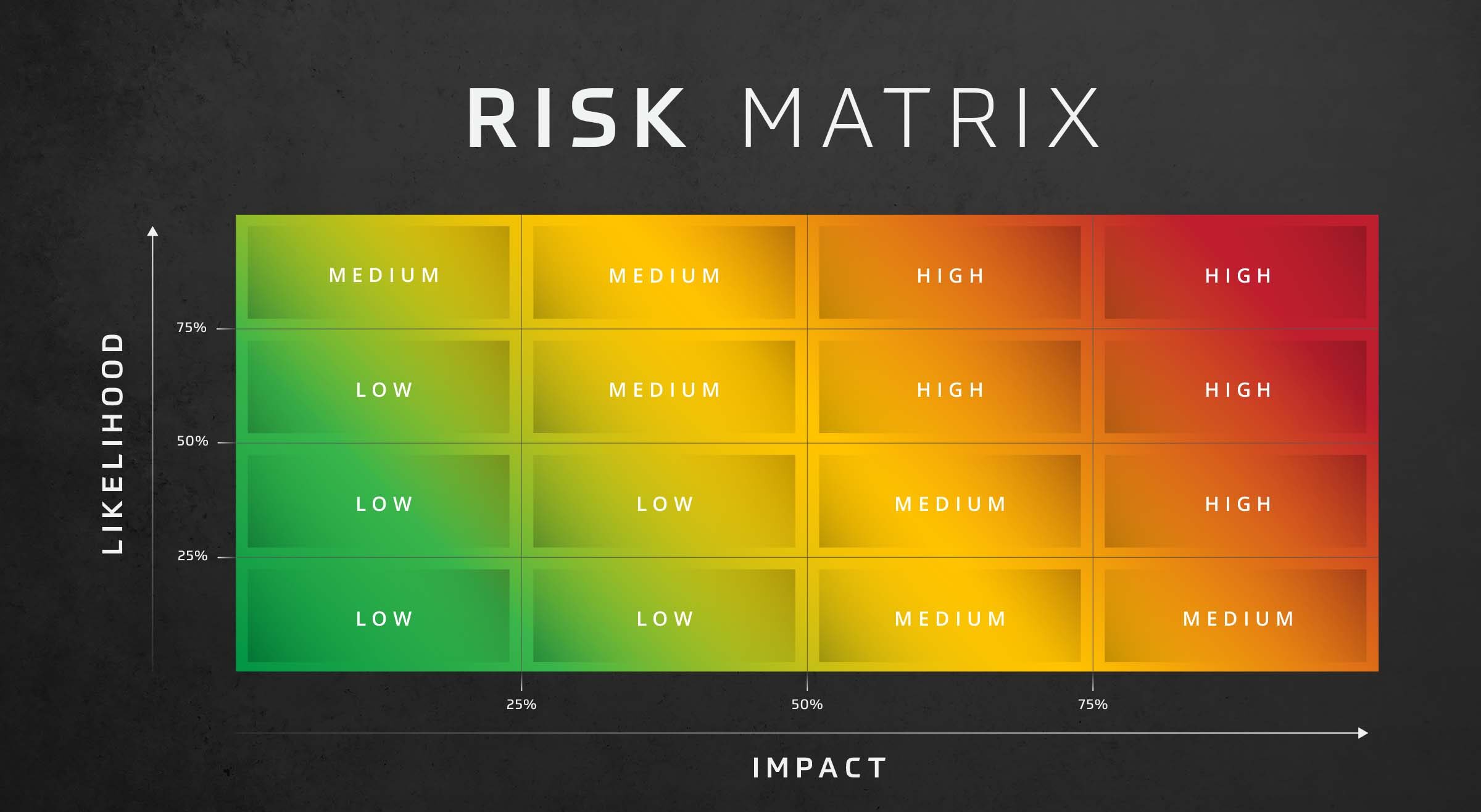
Risk Assessment: Likelihood and Impact
Assess risk effectively with the risk assessment likelihood and impact matrix. This decision-making matrix assesses risk based on the likelihood and impact of threats in your organization.
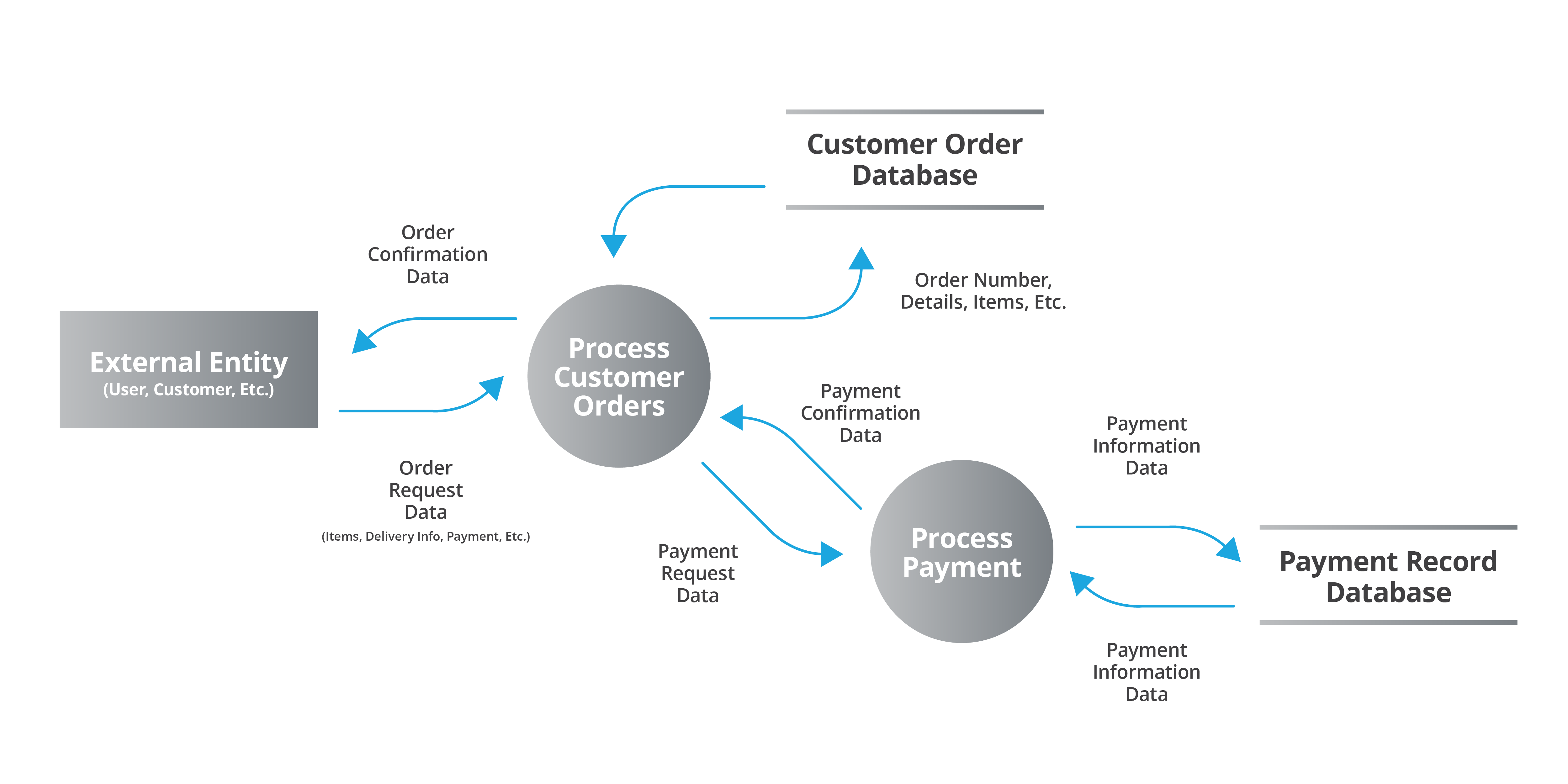
Why You Need a Data Flow Diagram (DFD)—and How to Create One
Data flow diagrams (DFDs) reveal risks, simplify complex systems, and enhance security. We’ll show you step-by-step guidance so you can create your own DFD.

SaaS Security: Don’t Allow Convenience to Compromise Your Data
Learn about the increased threat landscape in SaaS applications and the necessity to monitor and defend.