Infographic: Penetration Testing Explained
- Written by: Jordan Engbers
Penetration testing provides a real-world test of your security posture by sending an ethical hacker to break in using the same techniques as actual bad guys. While most people picture penetration testing as someone cracking lines of code, the process entails far more than that. Here's an overview of penetration testing explained from initial scoping to final validation.
Penetration Tester
Scoping
In this phase, clients and testers agree on the ground rules, such as whether the test of a web app extends to the infrastructure behind it. The team also decides whether to alert the client’s IT team about the penetration test or to let them practice stopping what they think is an actual attack.
Recon
Intel Gathering
Like real hackers, good penetration testers use the web, social media and other public sources to identify individuals and parts of the organization to target. They also uncover technical details through port scanning, network sniffing and more.
Vulnerability Scanning
Automated tools scan your system for known vulnerabilities such as open ports and unpatched software that the human pen tester can use in their attack.
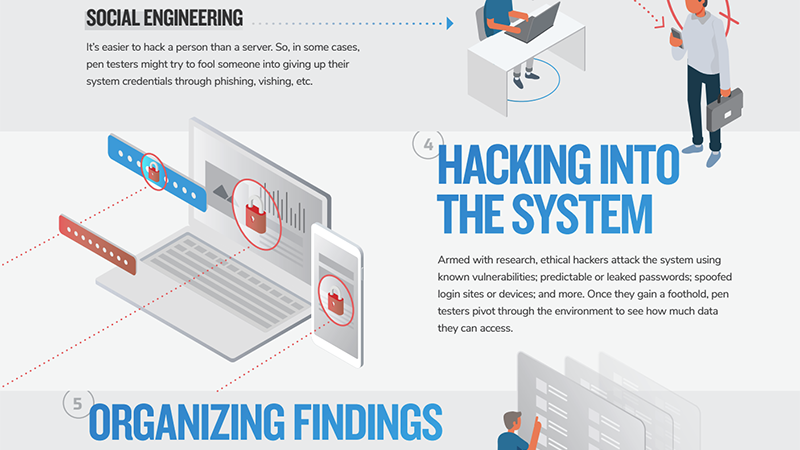
Social Engineering
It’s easier to hack a person than a server. So pen testers often try to fool someone into giving up their system credentials through phishing, pretexting phone calls, etc.
Hacking Into the System
Armed with research, ethical hackers attack the system using known vulnerabilities; predictable or leaked passwords; spoofed login sites or devices; and more. Once they gain a foothold, penetration testers pivot through the environment to see how much data they can access.
Organizing Findings
The pen tester begins listing risks they discover and categorizing them according to a common standard such as the OWASP Top 10 for web apps. Risk categories include broken access control, cryptographic failure, insecure design and more.
Reporting
Now the penetration tester formats their work into an understandable, actionable report for the client team. A good reporting process includes an executive summary, an in-depth technical report and an action plan listing recommended remediations.
Remediating
Armed with the detailed report, the client’s team can begin remediating moderate and high risks.
Validating
After the IT team remediates risks highlighted in the external portion of the penetration test, the pen tester returns to confirm that each risk has been eliminated. This confirmation is included as part of all external engagements.
Never miss a story
Get the latest technology insights from HBS, right in your inbox.
By entering your email, you agree to receive HBS emails and agree to our Terms & Conditions and Privacy Policy.