How a Hacker Conned an Accountant with $400,000 Phishing Attack
- Written by: Jordan Engbers

This is the true e-mail phishing story of a recent case. While the hacker got away with a partial victory this time, the case study can help you understand and prevent similar cyber attacks.
On a recent Friday afternoon (because isn’t it always?) the phone rang with a desperate-sounding professional services provider on the other end. “I think one of my clients just sent $400,000 to a hackers’ account. Can you help? ” It turns out they had sent the money. And we could help. And to help others learn from the very bad day experienced by one Accounts Payable employee (let’s call him Finance Guy) and his company (let’s call it Acme Corp), we’re providing a behind-the-scenes look at this phishing attack. Read on to see how the hacker got away with a small fortune for nearly a week—and how good incident response and digital forensics work got most of it back.
Lurking in the Network
Like most hackers, this one didn’t give himself away by grabbing the loot as soon as he got into the victim’s system. He slipped into an e-mail account at the victim company via a phishing attack, tricking Finance Guy into divulging his login credentials. (The hacker probably targeted Finance Guy specifically, knowing from his job title and LinkedIn profile that he had the ability to move money.)
After gaining access, the hacker spent several weeks monitoring Finance Guy’s e-mail messages to get a sense of his typical communication patterns and normal workflows.
Springing the Trap
After a few weeks, the hacker spotted their opportunity: an e-mail thread in which Finance Guy was discussing a payment of nearly $400,000 with a vendor. This information was time-sensitive, and the hacker understood that his window of opportunity was fleeting.
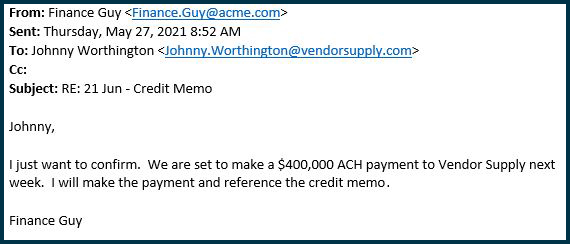
The hacker purchased a web domain that, if given only a quick glance, looked just like the vendor’s actual domain. Then the hacker created an e-mail address that closely matched the vendor’s, like this:
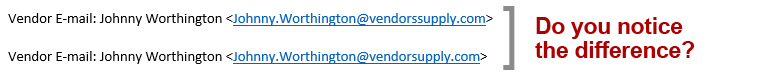
The hacker copied the real wire transfer e-mail thread out of Finance Guy’s e-mail account. Switching to the spoofed e-mail account, the hacker pasted the e-mail thread into a new e-mail and matched the subject line. The hacker sent the e-mail to the victim explaining that the previously shared bank account couldn’t receive payment due to an audit. The hacker helpfully offered a new bank account that could accept the payment.
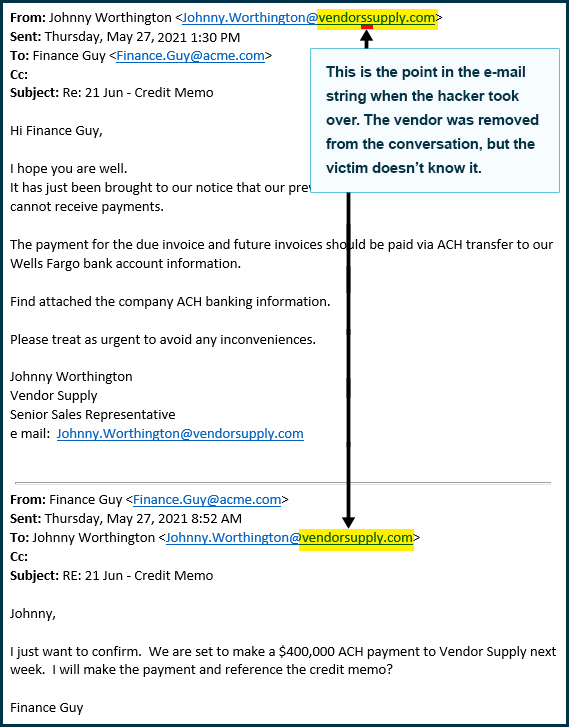
So Finance Guy unknowingly wired $400,000 to the hacker’s account.
The transfer was made on a Tuesday. And like all criminals that get caught, the hacker got greedy and decided to try for another payout. In the next couple of days, the hacker e-mailed Finance Guy (who still didn’t know he had been duped) to say that the original transfer didn’t work, and that Finance Guy needed to send the $400,000 to this “updated routing and account number.”
After seeing the third account number come through, Finance Guy became alarmed and called the vendor who was originally supposed to receive the transfer. The vendor, who hadn’t received any payment yet, knew nothing about the routing and account number changes. That’s when Acme’s team realized they had a big problem and called one of their financial service providers, who then called HBS.
Stopping the Damage
The HBS incident response team jumped into action. They immediately instructed the company to disable the compromised e-mail account and have the employee change all passwords. Examination of the e-mail chain discovered the spoofed e-mail address, and review of the e-mail logs revealed that the compromised e-mail account had logged in from Arizona. That’s a problem since Finance Guy works in Iowa.
HBS then assisted Acme with enabling multifactor authentication on all company e-mail accounts to prevent this type of incident in the future.
By working with law enforcement and the hackers’ bank, Acme recovered $320,000 of the $400,000 transferred to the hackers’ account.
What You Can Do to Stop This
Several cybersecurity best practices could have saved Acme the $80,000 that couldn’t be recovered, the cost of a digital forensics investigation and the notable stress of thinking they had lost $400,000. To prevent this kind of attack, HBS recommends:
- Multi-factor Authentication (MFA) – MFA could have prevented this entire incident, even if the hacker intercepted the victim’s e-mail login credentials. Without the second factor, the hacker couldn’t have gotten into the account, and the MFA prompt would have alerted the victim that someone was trying to access their account. They could have then immediately changed their e-mail account password.
- Employee training – This hacker was clever. The fraudulent e-mail address was extremely similar to the actual one. But an employee trained throughout the year on how to spot phishing e-mails probably would have checked the web address more carefully before clicking it.
- Procedures to avoid social engineering – When making a significant transaction, best practice is to pick up the phone and call the party you’re working with. That’s the old-school version of multifactor authentication: An e-mail backed up by a phone call.
- Managed XDR service – Managed Extended Detection and Response (XDR) tracks every activity in your system (including endpoints and cloud presence) and uses sophisticated machine learning, AI and rulebooks written by human analysts to detect threatening patterns. In this case, XDR almost certainly would have noticed anomalous behavior by whatever login credentials the hacker had compromised (including logging in from a different state). The system could have locked the account shortly after the hacker got in rather than giving the hacker weeks to conduct surveillance and hatch a scheme.
To help ensure your company doesn’t fall for this kind of phishing attack (or to get your response team in place for the day it does), contact HBS today.
Related Content

How to Train Employees With Simulated Phishing Campaigns
80% of security breaches stem from phishing attacks. Learn how to create an effective phishing campaign for your organization.

Hackers and ACH Fraud
Risk of fraudulent transactions has grown significantly. Learn how to prevent hackers from using Automated Clearing House (ACH) fraud to drain your accounts.

How to Spot Business Email Compromise
Learn how business email compromise attacks work, as well as the red flags you can use to spot an attack before falling for it.






