Remember to Review Your Data Loss Prevention Policies
- Written by: Dave Nelson
Data loss prevention (DLP), sometimes referred to as data leakage prevention, is a security strategy used to prevent end users from sending confidential information outside the organization. This is not a new problem, in fact it may be one the oldest problems in civilization. The only difference is our mediums for storing and distributing sensitive information. Instead of sealing our hand written scrolls with a stamp and wax and relying on our most trusted couriers to make delivery, we are purchasing DLP solutions and encrypting emails.
DLP Beyond the Technology
DLP software can be incredibly valuable in protecting confidential data. It affords us the ability to classify data and create business rules that restrict unauthorized users from accidentally or maliciously sharing our most confidential information. However, the real issue may not be with the technology but rather with our data loss prevention policies and with whom we are entrusting our most sensitive information.
Businesses are always striving to become more “efficient”, so they toss all of their data into shared folders and give global access to those folders. There are internal employees, contractors and vendors who often have unrestricted access to data they have no business controlling. The reality is that you can’t lose (or leak) data you don’t have. So, instead of relying solely on technology to help solve the problem, we challenge our clients to reconsider their data access policies and role definitions.
Consider reviewing your DLP policies before implementing a technical DLP solution
- Create and enforce a data classification policy. Classifying data, and then putting tighter controls around the most sensitive data, can greatly decrease the risk of data loss/leakage.
- Restructure access controls. Take a look at who needs access to data and why. This should be a routine process. As the business grows and matures, data access needs will change.
- Consider modifying roles and responsibilities. It's possible that the duties which require access to sensitive data could be consolidated into one role versus spread across multiple roles. This will certainly reduce exposure of sensitive data.
What You Can Learn From a DLP Policy Review
You may find that by following these suggestions you've reduced your risk to a point that implementing a large, complex DLP solution is no longer a sound investment. Perhaps minimal DLP controls on your email and internet connections will be sufficient. On the other hand, after working through the steps outlined above you may find that you need to implement even more technical controls. You could consider controls such as restricting access to USB mass storage devices or adding encryption to individual files. Another option is to implement digital rights management (DRM) to files, which allows you to restrict the rights to open, modify, print, copy, email, upload or take other actions on restricted documents.
One thing is for sure. Businesses that implement DLP solutions without reviewing and updating their data classification standards and DLP policies haven't really reduced their risk. They've simply masked it.
Related Content

10 Must-Have Information Security Policies
These 10 critical information security policies are weak (or missing) in most organizations. Start improving your security with these must-haves.
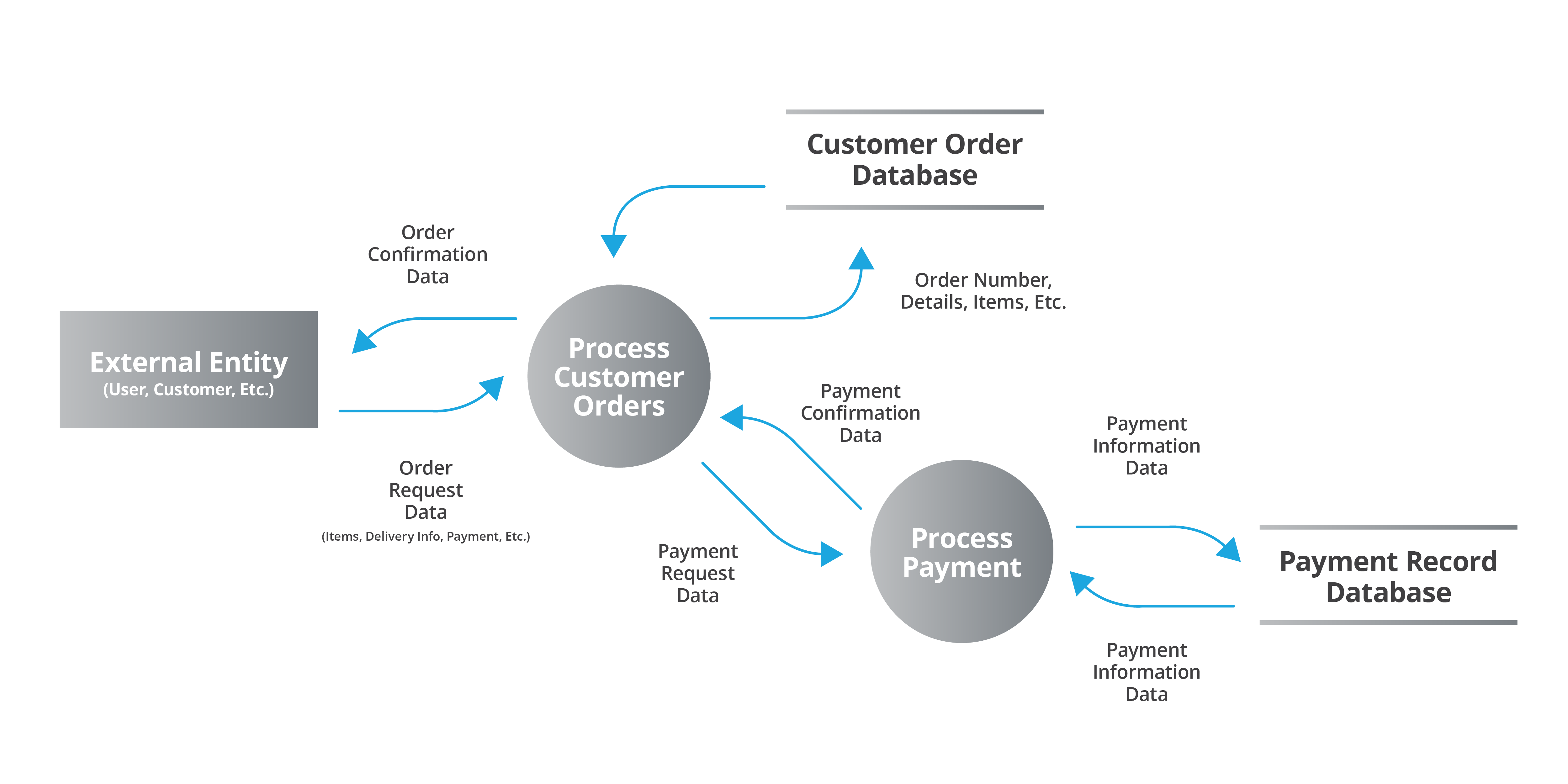
Why You Need a Data Flow Diagram (DFD)—and How to Create One
Data flow diagrams (DFDs) reveal risks, simplify complex systems, and enhance security. We’ll show you step-by-step guidance so you can create your own DFD.
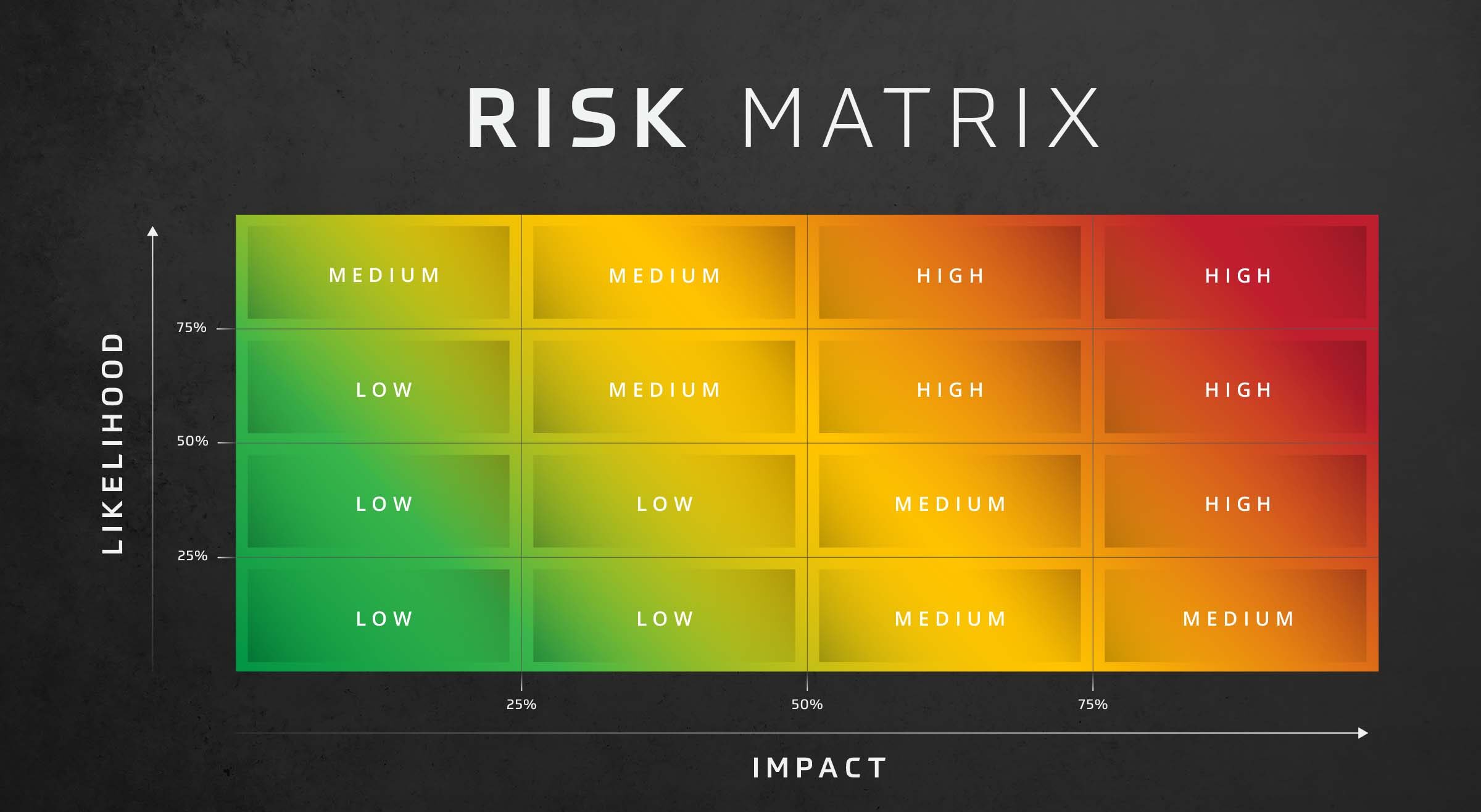
Risk Assessment: Likelihood and Impact
Assess risk effectively with the risk assessment likelihood and impact matrix. This decision-making matrix assesses risk based on the likelihood and impact of threats in your organization.