Beyond SIEM: How XDR Maximizes Threat Detection and Response
- Written by: Ryan Mosher

Security Information and Event Management (SIEM) systems operate on rule-based detection, identifying only known threats and often ignoring the nuanced or emerging dangers that pose the most risk. It is a reactive approach to security.
Cyberattacks are evolving faster than ever. Despite the numerous security tools organizations employ, many decision-makers are fooled by security theater—thinking they are completely secure when, in fact, those tools can rarely stop every threat—leaving a company lacking in their threat detection and response.
Getting bombarded with security alerts without the context to understand what’s real and what’s noise is like searching for a needle in a haystack—wasting valuable time and resources. A focus is required to sift the real dangers from the rest, otherwise you run the real risk of a serious breach occurring.
In fact, it takes, on average, 277 days to identify and contain a data breach with traditional security monitoring. That’s too long.
You need a more holistic and proactive threat response solution—Extended Detection and Response (XDR)—and we will talk about it.
Challenges of Traditional Security Monitoring (SIEM)
Traditional security monitoring tools are proving inadequate in the face of sophisticated cyber threats. Here's a deeper look into the limitations that make these conventional tools less effective:

- Limited Scalability: Many traditional tools struggle to handle large volumes of data effectively. As organizations grow and their data expands, these tools can't scale up efficiently, leading to potential gaps in monitoring and protection.
- Complex Deployment and Management:Setting up and maintaining traditional security systems often involves complicated configurations and ongoing management. This complexity requires significant time and expertise and increases the risk of human error, potentially leaving systems vulnerable.
- Slow Threat Detection: Traditional tools generally rely on rule-based detection mechanisms that can only identify known threats. This approach significantly delays the detection of new, never-before-seen threats, giving attackers more time to exploit vulnerabilities.
- Poor Integration and Data Correlation: These tools frequently operate in silos and struggle to integrate with other security solutions. This lack of integration hampers the correlation of security data across different sources, making it difficult to form a comprehensive view of security threats.
- Limited Real-Time Response: The response capabilities of traditional tools are often limited to sending alerts rather than taking direct action. This puts the onus on human operators to interpret alerts and execute responses, which can be too slow to counteract active cyber threats effectively.
- Lack of Contextual Awareness: Traditional tools can generate many false positives without a holistic view of the security environment. This wastes valuable security resources and makes it harder to spot genuine threats in the noise.
- Compliance-Centric Approach: Many traditional security monitoring tools are designed primarily to meet compliance requirements rather than to provide robust security. While compliance is necessary, this focus can divert attention from proactive threat detection and response strategies.
These challenges emphasize the need for a more robust approach to security monitoring that can adapt quickly, scale efficiently, and respond proactively to emerging threats.
XDR represents a leap forward in overcoming these limitations by offering an integrated, automated, and scalable solution designed for the complexities of today’s cybersecurity landscape.
SIEM + XDR: Holistic Threat Detection and Response
XDR is a cutting-edge solution that integrates various technologies and automation capabilities to empower threat detection and response across multiple domains, including email, data, endpoints, and identities.
These platforms are designed to overcome the limitations of traditional security tools by offering the following advanced features:
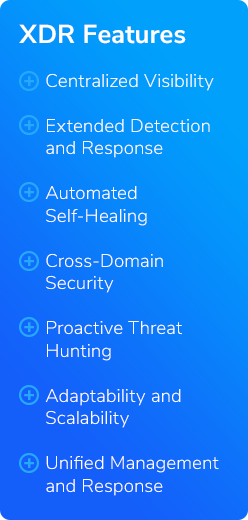
- Centralized Visibility: XDR provides a unified view of your security landscape, consolidating data from diverse sources into a single dashboard. This centralized visibility allows for easier monitoring and quicker identification of anomalies across all digital domains, enhancing the overall efficiency of the security operations center (SOC).
- Extended Detection and Response: Leveraging advanced analytics and machine learning, XDR goes beyond mere notification of threats. It actively analyzes vast data to identify patterns indicating a breach or attack. This capability enables the system to detect complex threats that traditional tools might miss, including zero-day exploits and advanced persistent threats (APTs).
- Automated Self-Healing: Upon detecting a threat, XDR doesn't just alert the relevant teams—it automatically initiates actions to mitigate and resolve security issues. This automated self-healing extends across various domains, from resetting compromised user credentials to isolating infected endpoints and applying security patches. This automation drastically reduces the response time and the burden on IT staff, allowing them to focus on more strategic tasks.
- Cross-Domain Security: By integrating defensive measures across email, applications, data, and devices, XDR breaks down the silos that typically exist in IT environments. This integrated approach ensures that security measures are coordinated and threats can be managed more effectively across all vectors.
- Proactive Threat Hunting: XDR enhances the security team’s proactive ability to hunt for potential security incidents before they escalate. With access to rich intelligence and contextual data, security analysts can craft advanced queries to uncover hidden threats, leveraging extensive threat intelligence networks.
- Adaptability and Scalability: XDR is designed to adapt to the changing landscape of cyber threats and the growing needs of businesses. Whether scaling up operations, adding new technologies, or integrating with existing systems, XDR accommodates an organization's evolving security requirements without compromising performance.
- Unified Management and Response: Integrating various security technologies under the XDR umbrella allows for a more streamlined management and response strategy. This unified approach not only simplifies the security management process but also improves the effectiveness of incident response through coordinated actions across all fronts.
By addressing the multifaceted challenges of modern cybersecurity with these sophisticated capabilities, XDR represents a substantial advancement in the tools available to organizations aiming to fortify their defenses against increasingly sophisticated cyber threats.
Managed XDR for the Best Threat Detection and Response
Using XDR, organizations can see their security tenant as a whole, improved by automatic reactions and connected protection systems across different domains.
This dramatically improves the speed and efficiency of threat detection and response, making your environment more secure.
But someone still has to run XDR.
A Managed XDR solution ensures that you have the best technology backed by the expertise of full-time security professionals. Around-the-clock monitoring and customized security playbooks are used to meet your organization's unique needs, scaling along with your growing business.
Managed XDR provides a comprehensive, proactive security strategy that minimizes risks, maximizes operational efficiency, and allows you and your team to focus time and resources on the things that move your business forward.
If you’re ready to enhance your organization’s security with a solution that truly protects you, contact HBS today.
Let us help you move from the illusion of safety to a real, effective, proactive defense.
Related Content

Managed XDR
Enhance security with Managed XDR from HBS: 24x7x365 SOC support, leveraging Microsoft Sentinel & Defender for proactive, adaptive threat defense and response.

XDR, MDR and EDR: What’s the Difference?
Discover the key differences between XDR, MDR and EDR solutions so you can ensure that you’re using the right tools to secure your environment.

How Managed XDR Makes the Most of the Latest Endpoint Protection Tools
Managed XDR helps endpoint detection reach its full threat-hunting potential as human experts tune the rules for ever-changing situations.